
Why mod_security Is Important And How To Install It
In this article, the machine used here is a CentOS 6.3, 64 bit, installed with Apache.
Why is mod_security important? It is important because no codes are perfect, and the Internet is a hostile place, filled with hackers who wanted to deface your website or maybe hijack your server’s resources to achieve whatever goals that they are trying to achieve. And they usually start with the web based application in your server, because this is the part of the server that is exposed to everyone in the world. There is nothing wrong with that in itself, because that is where your clients will come from, i.e. the world in general. While you may like to think that only your clients/staff are visiting your, the truth, your site will also be visited by people trying to hack into your site. Mod_security will help in detecting those hackers and stopping them.
So… let’s get started with installing mod_security.
Mod_security is not available in the repositories that come out-of-the-box when CentOS is installed. Additional repos need to be added.
Use the following command:
rpm -Uvh http://ftp.jaist.ac.jp/pub/Linux/Fedora/epel/6/x86_64/epel-release-6-8.noarch.rpm
Example:
[root@MyWebServer ~]# rpm -Uvh http://ftp.jaist.ac.jp/pub/Linux/Fedora/epel/6/x86_64/epel-release-6-8.noarch.rpm
Retrieving http://ftp.jaist.ac.jp/pub/Linux/Fedora/epel/6/x86_64/epel-release-6-8.noarch.rpm
warning: /var/tmp/rpm-tmp.ibjvOs: Header V3 RSA/SHA256 Signature, key ID 0608b895: NOKEY
Preparing… ########################################### [100%]
1:epel-release ########################################### [100%]
[root@MyWebServer ~]#
Now we can install mod_security.
Use the following command:
yum install mod_security
Example:
[root@MyWebServer ~]# yum install mod_security
Loaded plugins: fastestmirror, protectbase
Loading mirror speeds from cached hostfile
[lots of output not shown here]
Installed:
mod_security.x86_64 0:2.7.3-3.el6
Complete!
[root@MyWebServer ~]#
Important!
Mod_security is only as good as the rules it uses for scanning. Installing mod_security without any rules is useless (like installing an anti-virus without any virus signatures database). Most of us would not write our own rules. A default set of rules is available. Let’s install those rules as well.
Use the following command:
yum install mod_security_crs
Example:
[root@MyWebServer ~]# yum install mod_security_crs
Loaded plugins: fastestmirror, protectbase
Loading mirror speeds from cached hostfile
[lots of output not shown here]
Installed:
mod_security_crs.noarch 0:2.2.6-3.el6
Complete!
[root@MyWebServer ~]#
Restart Apache for the new configuration to take effect.
Is mod_security really working?
In this example, we created a test web page to represent a typical login page to a web application. In a production environment, that login page will submit the information to a script which then checks whether the user has keyed in the correct username and password. In our example, the script will merely display what is typed in the textboxes.
If mod_security is working, if we type in hacker-like strings into the textboxes, mod_security will catch it and prevent the strings from being submitted to the script.
A normal user will key in things like:

He clicks “Submit”, the script processes the information he submits. In this example, the script (add-record2.cgi) will merely display what he typed in. (In a production environment, the information submitted may be used to query a database, for example.)

A hacker, on the other hand, will try to be… “creative” with what he submits so that he can hack into the server. For example… (This is an example of what a simple SQL injection looks like.)

If mod_security is working, those dubious strings will not reach the script (add-record2.cgi). Mod_security will intercept it and display an error message.

Meanwhile, in the server’s logs, you will see lines like these, indicating that mod_security stopped something:
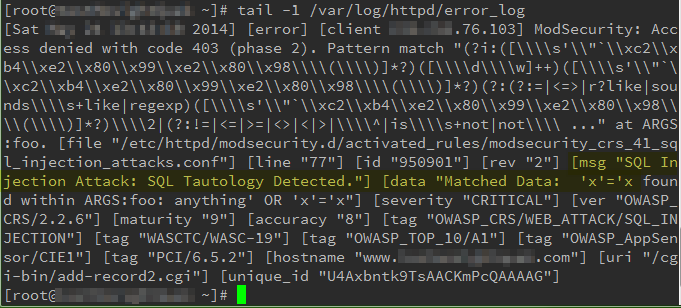
Of course, nothing replaces the good habit of writing scripts that knows how to properly “clean” information that is submitted to it before further processing. In the event that something in your web site’s application is vulnerable, mod_security might just be the only thing left to stop the hacker from doing damage to your server.



